Important Disclaimer: Software bugs are an inherent part of software development. They have always existed and will continue to exist due to the complexity of modern systems and the inherent limitations of human error. The presence of a bug does not necessarily indicate that a software product is fundamentally flawed or ineffective. Even the most rigorously tested and widely used software can contain bugs that may only surface under specific conditions. Please note that some technical details have been deliberately omitted in this document as it refers to a commercial software and could impact intellectual property. The following document must be considered partial and not exhaustive.
On July 19, 2024, CrowdStrike, a leading cybersecurity firm renowned for its Falcon platform, encountered a significant operational disruption stemming from a faulty update to its Falcon Sensor software for Windows systems. The incident, which unfolded at approximately 4:09 UTC, led to widespread system crashes and the dreaded blue screen of death (BSOD) on affected devices. This unforeseen event caused substantial disruption to businesses and organizations worldwide that relied on CrowdStrike’s Falcon platform for robust endpoint protection. The root cause of this incident has been traced to a configuration update within the Falcon Sensor, specifically one that altered how the software evaluated named pipe execution on Windows systems.
Named pipes serve as a crucial inter-process communication mechanism in Windows, and the update intended to enhance security measures against malicious named pipes commonly exploited in cyberattacks. However, the update inadvertently introduced a critical flaw that triggered a logic error within the Falcon Sensor, ultimately leading to system failures. Upon discovering the issue, CrowdStrike worked to address the faulty update. By 5:27 UTC on the same day, a remediation fix was deployed, and the company shifted its focus to restoring the affected customer systems. CrowdStrike has categorically assured its customers that this incident was not a cyberattack and that the security and integrity of their Falcon platform systems remain uncompromised.
Further investigation into the incident revealed that the problematic configuration update, known as “Channel File 291,” aimed to bolster the Falcon Sensor‘s ability to detect and neutralize malicious named pipes employed by common command-and-control (C2) frameworks in cyber-attacks. Named pipes are often leveraged by threat actors to establish communication channels with compromised systems and orchestrate their attacks. However, the update’s implementation contained a critical error in its logic, which caused the Falcon Sensor to malfunction and trigger system crashes upon encountering specific named pipes.
TECHNICAL INSIGHTS
The technical cause of the BSODs in the CrowdStrike incident stemmed from a critical error within the configuration update known as Channel File 291, which is processed and ingested by the CSAgent.sys driver.
This driver is a core component of the Falcon Sensor, responsible for managing its interaction with the Windows operating system kernel. The update aimed to enhance the Falcon Sensor’s ability to detect and mitigate threats associated with malicious named pipes, which are often utilized in command-and-control (C2) communication by cyber attackers.
At this point it is already possible to formulate some hypotheses as to how, potentially, updating one of these channel files could have caused the systems crash.
Flawed Named Pipe Handling: The updated logic in Channel File 291 might have introduced bugs in how CSAgent.sys handles named pipe objects. If the code did not properly check for null pointers before accessing or manipulating named pipe structures, it could have resulted in null pointer dereferencing. This would occur when the code tries to read or write data from a memory location pointed to by a null pointer, which is invalid and causes a crash.
Allocation Failure: If the update caused an error in memory allocation related to named pipe structures, a null pointer could be returned, and subsequent attempts to use this unallocated memory would trigger a crash.
Uninitialized Pointers: If the update introduced changes that left pointers to named pipe structures uninitialized or set to null under certain conditions, subsequent attempts to use these pointers without proper checks would lead to null pointer dereferences and crashes.
CSAgent.sys
The CSAgent.sys file is a kernel-mode driver that is part of the CrowdStrike Falcon sensor software. According to technical insights, resulting from static analysis, it seems to be responsible for a variety of tasks, including:
File System Minifilter Driver: The driver registers callback routines with the filter manager to intercept and potentially modify file system requests. This is a common technique used by security software to monitor and control file access.
Event Tracing for Windows (ETW): The driver uses ETW to log events and send telemetry data. This is a standard Windows mechanism for logging diagnostic information.
Inter-Process Communication (IPC): The driver creates a device object (named “\Device\csagent“) that can be used for communication between user-mode and kernel-mode components of the CrowdStrike software. It also uses a custom protocol for IPC, which involves creating and managing communication channels (referred to as “channel files“).
Thread and Synchronization Management: The driver creates and manages threads, likely for performing background tasks. It also uses synchronization objects (like locks and events) to coordinate the activities of different threads.
Memory Management: The driver allocates and frees memory pools, likely for storing data structures and buffers used for IPC and other operations.
Registry Access: The driver reads and writes values to the Windows registry, probably for storing configuration settings and persistent state.
Cryptographic Operations: The driver makes use of cryptographic functions (like hashing) for security purposes, such as verifying the integrity of files or messages.
Network Communication: The driver appears to be involved in network communication, possibly for sending telemetry data to CrowdStrike’s cloud service or receiving updates.
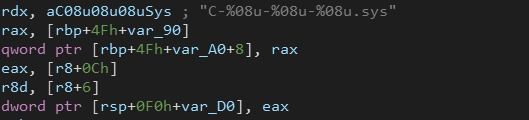
As I can observe, the driver’s code is much complex and highly optimized with extensive error handling. The presence of features like file system filtering, event tracing, and cryptographic operations suggests that it plays a crucial role in the security and monitoring capabilities of the CrowdStrike Falcon sensor. The channel files (referred in the code as C-%08u-%08u-%08u.sys) appear to be a key component of the driver’s IPC mechanism. They are used to establish communication channels between different components of the CrowdStrike software.
The driver’s code includes functions for creating, opening, closing, reading from, and writing to these channel files. The channel files are likely used to exchange commands, data, and status information between the user-mode and kernel-mode components of the software. The driver’s interaction with the channel files is complex and involves various synchronization mechanisms to ensure the integrity and consistency of the data being exchanged. Furthermore, the driver uses locks to protect critical sections of code and events to signal the completion of asynchronous operations.
The driver also uses a custom protocol for framing and interpreting the messages exchanged over the channel files (its analysis goes beyond the scope of this document). Understanding the driver’s IPC mechanism and its interaction with the channel files is crucial for troubleshooting issues like a potential null pointer dereference or unmapped memory regions. Indeed the crash could be caused by a bug in the driver’s code that leads to an invalid memory access when reading from or writing to a channel file. It could also potentially be caused by a race condition between different threads accessing the same channel file concurrently.
According to information collected, I focused my analysis on the functions mainly responsible to handle and interact with channel files. Some of these are reported below (I will not delve in details of specific capabilities and I am going to mask the complete function reference as here we are talking about a commercial software):
sub_14000****: This function appears to be a cleanup function for a data structure. It takes a pointer to a data structure (likely the channel communication structure). It appears to decrement a reference counter (potentially associated with the device object) and, if the flag is set, frees the memory allocated for the data structure.
sub_14000****: This function appears to initialize a communication channel. It takes a pointer to a kernel-mode structure and a pointer to a channel pointer. If the channel already exists, the function returns a pointer to it. Otherwise, it allocates memory for a new channel structure, initializes it, and returns a pointer to it. If memory allocation or initialization fails, it returns an error code.
sub_14000****, sub_14000****, sub_14000****, sub_14000****: These functions appear to specifically create novel communication channels. They takes a pointer to an input buffer and a pointer to a channel pointer. It allocates memory for a new channel structure, initializes it with data from the input buffer, and returns a pointer to it.
POTENTIAL CAUSE
I focused my analysis over a specific function responsible to handle the writing of data to a communication channel. It operates on a complex data structure, probably an IRP (I/O Request Packet), which contains information about the I/O request and a data buffer. The function iterates through an array of structures, each representing an element to be written into the channel.
For each element, the function performs a series of checks and specific operations based on the element’s type. However, one of the variable appears to be a pointer to a data structure used to track write operations. The crash appears to happen in a code fragment part of this larger function that seems to handle the processing of channel files in the CrowdStrike Falcon sensor driver.
These specific instructions are responsible for reading a value from a data structure within the channel file, where the register r8 is expected to hold a pointer to this data structure.
I prepared a pseudo-code representing the code fragment with comments:
...[redacted]...
if (r8 != NULL) { // Check again after acquiring the lock
r9d = *(int*)(r8); <- CRASH HERE !!!
} else {
// Handle the error (e.g., return an error code, log the error)
}
release_lock(channel_file_lock); // Release the lock after accessing the channel file
} else {
// Handle the error (e.g., return an error code, log the error)
}
...[redacted]...The code implement a NULL Pointer check at the beginning. The crash, manifesting as a BSOD due to an unreferenced address in register r8, could be caused in my opinion by two main factors:
Incorrect Offset Calculation: The updated channel file caused a wrong calculation of an offset within a data structure or an array pointed to by rax. If the value in r11 is incorrect the resulting address in r8 could be invalid, pointing to an unreferenced memory region.
Channel File Corruption / Inconsistent Data: If the channel file itself is corrupted or invalid can lead to an unreferenced address when the driver tries to read from it.
The channel files appear to be in proprietary format and their analysis is beyond the scope of this document.
CONCLUSIONS
The CrowdStrike “Falcon Sensor” issue highlights the challenges inherent in the complexity and interconnectedness of modern systems. The intricate nature of modern security software, with their multiple functionalities and interactions with various system components, makes them potentially susceptible to errors and vulnerabilities. More generally speaking, this event underscores the challenges posed by the increasing complexity and interconnectedness of modern systems. It emphasizes the importance of robust software development practices, thorough testing, and comprehensive understanding of complex codebases to ensure system stability and security.