
On July 1, 2024, the cyber security vendor Halcyon, Inc., identified a novel ransomware strain they named LukaLocker (ref. here). In the article researchers from Halcyon reported a new ransomware operator, dubbed Volcano Demon, specialized in attacks using the LukaLocker encryptor. According to the source, the threat actor targets both Windows and Linux systems, demonstrating its versatility and potential for widespread infections. Similarly to other threat groups, Volcano Demon encrypts files on infected devices, rendering them inaccessible to their owners. To regain access, victims are presented with a ransom demand, often accompanied by a threat to release stolen data if the payment is not made.
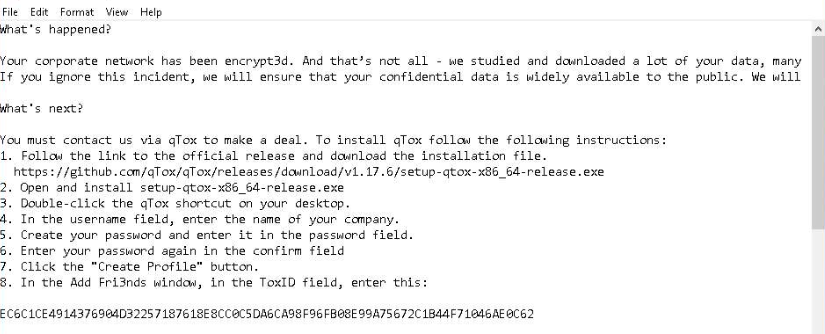
LukaLocker Ransomware Ransom Note
Starting by observing a LukaLocker sample (sha256:30390db8ef77afdb6add86f7f2990a142823401078ab237020933d0423374b27) I found several code overlaps with another piece of malware (sha256:d949cc181b6163bd4f1717d0218b993d9009c79e45aff578946ebe79e82974da) after creating several code-based hunting YARA rules. Specifically, pieces of code on the sub_14003AF50 in LukaLocker sample appears to be almost identical to the sub_233837F50 of the second sample. Generally speaking, based on the analysis of both files, the most distinctive and developer-specific functions often revolve around:
-> Usage of function pointers and dynamic code execution techniques.
-> Custom string parsing and obfuscation mechanisms.
-> Dynamic memory management routines tailored for low-level operations.
-> Conditional execution flows involving specific branching patterns and bitwise manipulations.
Both malware samples contain complex string parsing routines crafted to obfuscate or transform strings at runtime. These functions often handle encoded or obfuscated strings, decoding them only when needed to perform specific operations.
// Example of common string parsing pattern
while (1) {
char c = *strPtr++;
if (c == '_') {
if (strncmp(strPtr, "GLOBAL", 6) == 0) {
// Unique bitwise checks here
strPtr += 6;
continue;
}
} else if (c == 'Z') {
// Unique pattern checks
handleZPattern(strPtr);
break;
}
}
This string parsing approach is unique due to its specific sequence checks and conditions that align with the developer’s need to obfuscate commands or internal strings, allowing them to remain hidden from static analysis. Another recurring pattern in both files involves manually allocating memory using low-level functions like alloca or VirtualAlloc, followed by direct manipulation.
// Dynamic memory management pattern
size_t length = calculateLength(inputString);
if (length > 0x800) {
return 0;
}
void *memBlock = alloca(length * 32); // Allocate a block of memory dynamically
memset(memBlock, 0, length * 32);
// Custom logic to populate or manipulate this block based on input
processMemoryBlock(memBlock, length);
This structure is crafted for dynamic handling of data. The memory operations are typical of malware that requires fine-grained control over its allocated space, such as for shellcode execution or payload manipulation. Finally, both samples use complex conditional logic with bitwise operations to control execution flow. This pattern is not typical in benign software and is often used to add layers of conditional obfuscation, making the flow of execution less predictable.
unsigned __int64 flags = 576460752303424513; // Custom bitmask setup seen in both files
if (_bittest64(&flags, (unsigned int)(unsigned __int8)*strPtr - 36)) {
int checkResult = checkConditions(strPtr);
if (checkResult) {
executeObfuscatedRoutine(checkResult, additionalParam);
}
}
The shared characteristics between the two malware files suggest that they are related, either as variants of the same malware family or as products of the same development toolkit or actor. Specific aspects like the consistent use of low-level operations, shared subroutine logic, and identical obfuscation tactics support this hypothesis. Indeed, the high degree of code reuse indicates that the malware developers are likely reusing their own code across different projects. This is a common practice among malware authors to save development time and maintain a consistent operational profile. The distinct style of obfuscation, specific API usage patterns, and function naming conventions provide valuable indicators for attributing the malware to a particular developer or group.
The Nitrogen Campaign
The Nitrogen malware campaign is an advanced and targeted cyber-attack primarily focused on initial access operations that lead to ransomware deployment. The campaign employs a sophisticated malvertising strategy, leveraging Google and Bing search ads to promote fake software download sites. These ads are cleverly disguised as legitimate tools such as AnyDesk, Cisco AnyConnect, PuTTY, and FileZilla, which are commonly used by IT professionals and administrators. This tactic exploits user trust in well-known software, luring them into downloading trojanized installers that include malicious payloads. Once a user clicks on one of these ads, they could be redirected to compromised WordPress-hosted pages designed to mimic the legitimate download sites of the targeted software. Depending on geographic location and other factors, some visitors are further redirected to benign decoy sites to avoid detection by security researchers. However, targeted victims receive trojanized ISO files containing both the legitimate software installer and a malicious Dynamic Link Library (DLL). This file serves as the Nitrogen malware installer which implements DLL sideloading techniques to run the payload. The Nitrogen executes the legitimate software to avoid user suspicion while simultaneously deploying a hidden, malicious Python package (called NitrogenStager). This component is responsible for establishing communication with the command-and-control (C2) server, launching Meterpreter shells, and/or deploying CobaltStrike beacons on the compromised systems. These tools facilitate remote access and further exploitation, including data theft and ransomware deployment. Nitrogen infections in the recent past leaded to the deployment of BlackCat/Alphv ransomware. The NitrogenStager uses advanced evasion techniques, such as DLL preloading and encryption using AES, with hardcoded keys to maintain stealth and avoid detection by endpoint security measures. Further details about Nitrogen can be found on the Sophos blog (ref. here).
BlackCat / Alphv TakeDown
In December 2023, the FBI announced a significant disruption of the BlackCat / Alphv group, seizing multiple websites and releasing a decryption tool to aid victims. Following the FBI’s action, reports suggested that BlackCat may have temporarily ceased operations after receiving a large ransom payment from Optum, a major healthcare company. However, the group’s representative claimed they were merely re-evaluating their strategies rather than permanently shutting down. Regardless of the group’s claims, the LE operation had significant implications for its affiliates, potentially pushing them to seek alternatives. Following the disruption, BlackCat‘s reputation has been adversely affected, which may lead several affiliates to reassess their affiliation to the group. In this context, it is possible to hypothesize that some of these affiliates, who previously relied on this R-a-a-S (Ransomware-as-a-Service), may have thought of valid alternatives, perhaps including the development of a proprietary locker.
The LukaLocker Ransomware
As reported at the beginning of this article, on July 01, 2024, Halcyon, Inc. reported LukaLocker as a novel ransomware threat (ref. here) served by an adversary named Volcano Demon. In addition to what has already been technically reported by the Halcyon‘s analysis, LukaLocker repackages features likely derived/copied from the leaked Conti source code with some minor differences.
Conclusions
In relation to the extracted technical evidence, it is possible to hypothesize a probable origin of the locker in question as well as potential conditions that have led to its development. The most likely hypothesis is that the authors of the Nitrogen malware campaigns were former affiliates of the BlackCat / Alphv group (as the infection chain based on it ended with the delivery of this ransomware on late 2023) who then decided to evaluate alternative solutions following the LE action against BlackCat / Alphv. In this regard, the development of the LukaLocker ransomware began, taking inspiration from the leaked Conti source and reusing some code fragments already included in Nitrogen. Other scenarios could however be plausible such as one where an independent malware developer was commissioned for two different projects (however the latter is to be considered much less likely in my opinion).