In recent days, the FBI was entrenched in a virtual struggle against the ransomware group known as ALPHV / BlackCat. This engagement unfolded subsequent to the FBI gaining control of the underlying infrastructure that the group had utilized to amass over $300 million in ransoms. In the early hours of Dec. 19, 2023, the darkweb website associated with BlackCat DLS (Dedicated Leak Site) started showing a banner explicitly indicating its seizure as result of a join law enforcement operation.

Simultaneously, the Justice Department disclosed its intervention in disrupting the BlackCat‘s operations by deploying a decryption tool. This tool empowers approximately 500 identified victims to initiate the restoration of their systems and data. The overarching financial impact reveals that BlackCat extorted an estimated $300 million from around 1,000 victims.
According to OSInt information reported, the FBI agents acquired 946 private keys crucial for hosting victim communication sites. These keys seem to have been obtained with the collaboration of a human source who responded to an advertisement on a publicly accessible online forum, soliciting applicants for BlackCat affiliate positions. Within few hours from the seizure, however, the seizure notice has been replaced with another one declaring, “This website has been unseized.” (reported below). Crafted by BlackCat operators, the new notice likely aimed to mitigate the perceived impact of the FBI’s intervention.
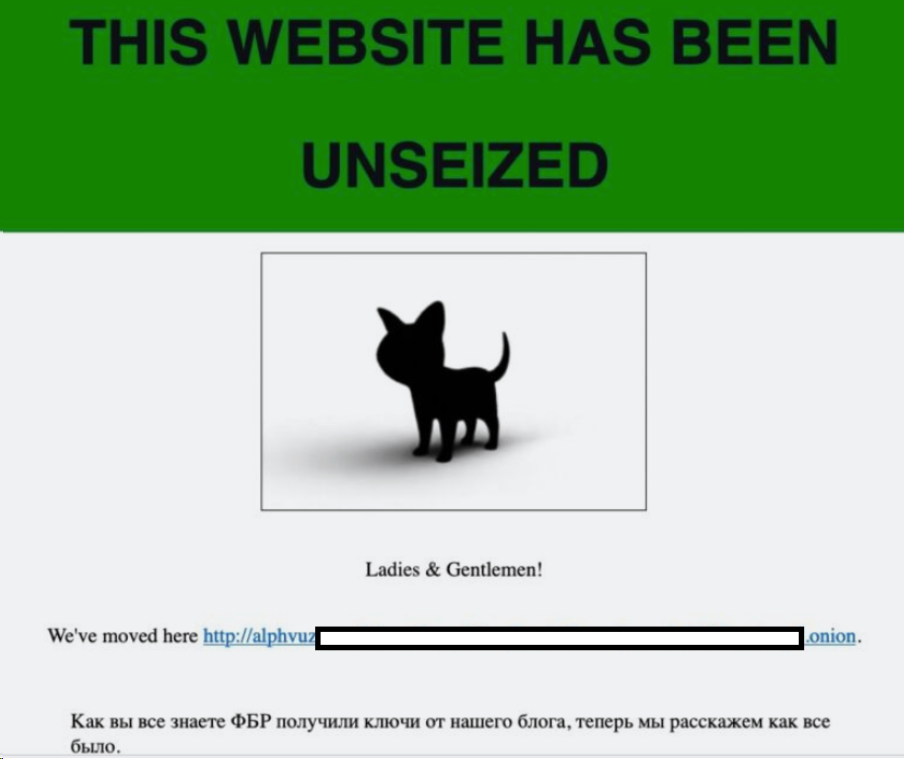
While acknowledging the effectiveness of the decryptor tool for 400 victims, BlackCat officials sought to downplay the overall significance of the disruption. In a calculated response, they asserted that the FBI’s actions would impede the decryption process for data belonging to an additional 3,000 victims.
In their ‘unseizure‘ communication, BlackCat disclosed a new TOR URL for their Dedicated Leak Site, strategically designed to elude any potential seizure by the FBI due to the absence of private keys. At this point the question is: how was it possible for the BlackCat operators to ‘unseize‘ the seized .onion website ?
IT’S A HASH TABLE MATTER
The way that domain resolution works for .onion services is through a Distributed Hash Table (DHT). The DHT is a decentralized system that enables nodes to store and retrieve key-value pairs. In the context of TOR‘s .onion services, the DHT is used to store the descriptors of the hidden services, allowing clients to reach them.
When a hidden service publishes its descriptor to the DHT, it signs the document with a key represented by its domain name (addresses in the onion TLD are generally non-mnemonic, alpha-numerical strings which are automatically generated on the basis of a public key when an onion service is configured.)
The process of updating the DHT involves publishing the descriptor to the responsible HSDirs (in the TOR network, HSDir, which stands for Hidden Service Directory, is the component responsible for storing and delivering descriptors for onion services to clients.), which are calculated based on the descriptor ID and an ordered list of HSDir fingerprints. The DHT is updated by the hidden service publishing its descriptor to the designated nodes, and this process is repeated periodically.
To take control over a .onion site, we would need to demonstrate control of the .onion address, which is the public key, by owning the private key. This control allows us to submit an entry to the TOR network to direct traffic to the address. The specific keys required for this control are the private key associated with the .onion address.
By owning this private key, an entity can prove its control over the .onion address and consequently manipulate the DHT to direct traffic to a specified location. In fact, the DHT in the context of TOR‘s .onion services is a fundamental component that enables the decentralized storage and retrieval of hidden service descriptors, facilitating the anonymity and accessibility of these services within the TOR network.
THE {BLACK}CAT AND MOUSE GAME
First of all, it’s to clarify that BlackCat / Alphv operatos technically did not ‘unseized’ anything and, on the other hand, the FBI technically did not “hacked” anything.
According to FBI’s disclosed information in fact, law enforcement operators were able to retrieved a total of 946 public / private key pairs utilized by the ALPHV / BlackCat ransomware group to manage their diverse .onion services. Acquiring the private key corresponding to a .onion website does not inherently constitute “hacking” in the traditional sense, as it involves obtaining the legitimate means of authentication for the site.
In the context of TOR’s .onion services, the private key is intricately linked to the .onion address and is used for authentication. This means that possession of the private key allows for control over the .onion site and the ability to prove ownership of the site’s address. In few words, the acquisition of private keys and subsequent manipulation of the DHT could result in the disruption of service availability for .onion websites.
These days, therefore, two entities (the FBI and the BlackCat‘s operators) are in possession of the keys to control various .onion services and there is nothing stopping the gang from updating the DHT in its turn after the FBI‘s seizure of the latter. Indeed, if multiple entities possess the private key corresponding to the domain name, a scenario arises where the last entity to submit its entry to the Distributed Hash Table (DHT) gains precedence.
This situation, as said, has been exploited by the ransomware group by configuring their server to aggressively submit their entries into the DHT. However, it is important to note that law enforcement also holds the private key, providing them with the capability to counter such tactics and submit their update even more aggressively.
This dynamic creates a scenario where the control and manipulation of the DHT entries become a strategic interplay between the ransomware group and law enforcement and this fight is crucial to gain influence in the network.
CONCLUSIONS
The possession of private keys has emerged as a strategic factor in this battle. The event highlighted a battle hidden from the eyes of most but not unimportant for the exercise of influence in the digital underground. This dynamic has significant implications for both ransomware operators and law enforcement agencies.
In fact, the ransomware group may seek to aggressively submit their entry into the DHT, while law enforcement, having gained visibility into the group’s network and possessing the private key, can employ counterstrategies to assert their influence within the Tor network. The possession and strategic use of private keys introduce a complex and dynamic dimension to the battle between law enforcement and ransomware operators.
More generally speaking, it underscores the criticality of private key management and its impact on the operational dynamics of .onion services. As law enforcement agencies continue to disrupt ransomware operations and gain insights into the infrastructure supporting such activities, the strategic interplay surrounding the TOR‘s technicalities becomes a pivotal aspect of the ongoing battle against ransomware.